keepalived
Keepalived概念
前置知识LVS,点我转到LVS
Keepalived最初是为LVS而设计,用于避免LVS的单点故障(只有一台LVS服务器,当它Down之后整个集群就崩溃了)。该项目主要是为了Linux系统和基础设施提供简单而强大的负载均衡和高可用性,Keepalived中的负载均衡框架依赖与LVS(IPVS)内核模块,提供4层(OSI七层模型中的第四层)负载均衡。
简单来说,Keepalived是LVS的升级版,在此基础上增加了故障检测和**高可用(VRRP)**功能,之前我们配置LVS的时候是使用ipvsadm软件包来进行设置的,但使用keepalived之后就无需通过ipvsadm进行配置管理,更多的是用来查看LVS的配置。
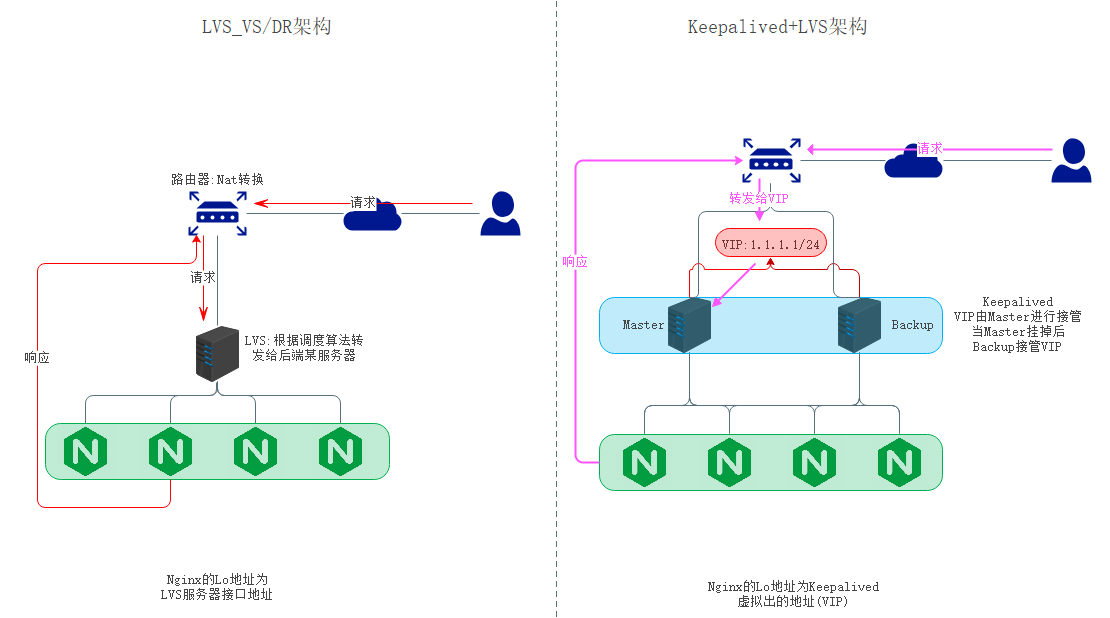
如上图所示:
- 传统LVS实现Web应用的高可用,但是LVS存在单点故障。当LVS服务器Down掉之后,整个集群将瘫痪无法对外提供服务。
- Keepalived+LVS架构解决了LVS存在的单点故障并提供负载均衡、高可用性。当Master节点Down掉之后,Backup发现之后就会代替Master接管VIP的工作
- Keepalived节点可以任意台(大于等于2)
配置文件解析
Keepalived配置分为三大模块
1 | global_defs{ |
默认配置文件:
1 | ! Configuration File for keepalived |
实验
keepalived部署及配置
实验拓扑
由两台服务器共同维护一个VIP,VIP正常情况下由Master接管,当Master发生故障后由Backup代替接管
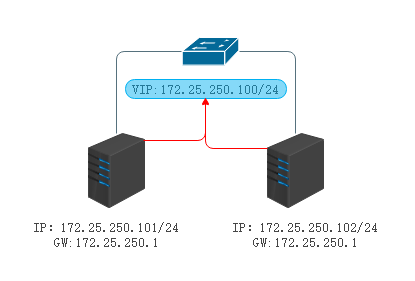
IP地址配置(略)
Master配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45[root@backup ~]# systemctl disable --now firewalld
[root@master ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:73:6d:58 brd ff:ff:ff:ff:ff:ff
inet 172.25.250.101/24 brd 172.25.250.255 scope global noprefixroute ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe73:6d58/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@master ~]# dnf -y install keepalived
[root@master ~]# cd /etc/keepalived/
[root@master keepalived]# cp keepalived.conf keepalived.conf.bak
[root@master keepalived]# vim keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
# 邮箱列表没有不写
}
router_id master # 路由表示设置为主机名
vrrp_skip_check_adv_addr
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state MASTER # 状态设置为master
interface ens33 # 绑定接口为ens33
virtual_router_id 51 # 虚拟路由IP
priority 100 # 优先级
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.250.100 # VIP
}
}
[root@master keepalived]# systemctl enable --now keepalivedBackup配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38[root@backup ~]# systemctl disable --now firewalld
[root@backup ~]# dnf -y install keepalived
[root@backup ~]# cd /etc/keepalived/
[root@backup keepalived]# ls
keepalived.conf
[root@backup keepalived]# mv keepalived.conf keepalived.conf.bak
这里我就不修改了直接拷贝Master的配置文件过来
[root@backup keepalived]# scp root@172.25.250.101:/etc/keepalived/keepalived.conf .
root@172.25.250.101's password:
keepalived.conf 100% 424 233.5KB/s 00:00
[root@backup keepalived]# vim keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
}
router_id backup # 路由ID改为主机名
vrrp_skip_check_adv_addr
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state BACKUP # 状态为备用
interface ens33 # 接口
virtual_router_id 51 # 虚拟路由ID,同于一个vrrp组需一样
priority 99 # 备节点需比Master优先级低
advert_int 1
authentication {
auth_type PASS
auth_pass 1111 # 密码验证
}
virtual_ipaddress {
172.25.250.100 # VIP
}
}
[root@backup ~]# systemctl enable --now keepalived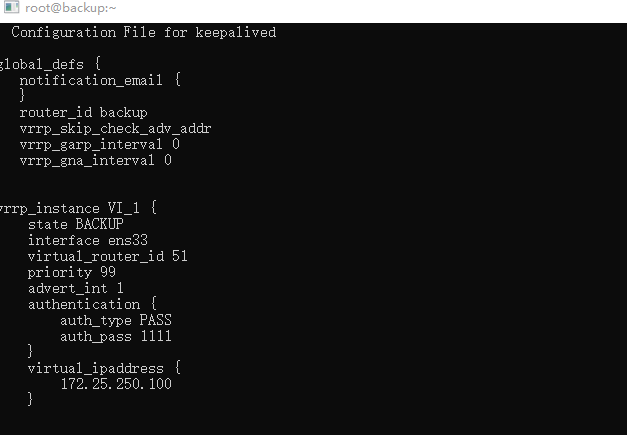
验证阶段
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32[root@master ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:73:6d:58 brd ff:ff:ff:ff:ff:ff
inet 172.25.250.101/24 brd 172.25.250.255 scope global noprefixroute ens33
valid_lft forever preferred_lft forever
inet 172.25.250.100/32 scope global ens33 # VIP
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe73:6d58/64 scope link noprefixroute
valid_lft forever preferred_lft forever
-------------------------------------------------------------------------------------------
[root@backup ~]# ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:b7:ea:f8 brd ff:ff:ff:ff:ff:ff
inet 172.25.250.102/24 brd 172.25.250.255 scope global noprefixroute ens33
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb7:eaf8/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@backup ~]#
通过ipadd命令查看,可以发现VIP由master接管
------------------------------------------------------------------------------------------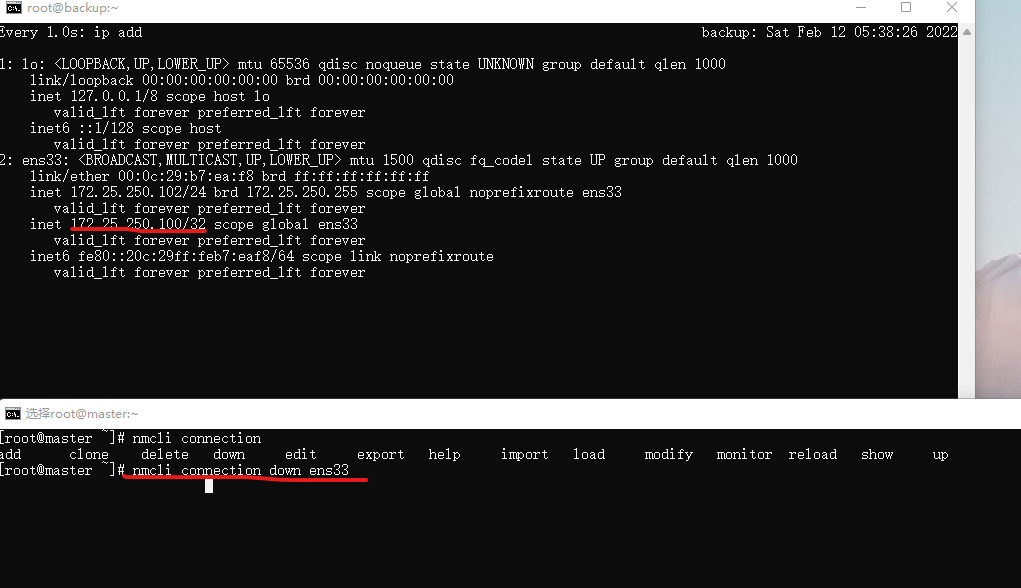
当我主动断开master网卡接口之后,172.25.250.100被backup接管
分析日志
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30[root@backup ~]# tail -n 50 /var/log/messages
Feb 12 05:30:02 backup Keepalived_vrrp[1141]: (VI_1) Sending/queueing gratuitous ARPs on ens33 for 172.25.250.100
Feb 12 05:30:02 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:30:02 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:30:02 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:30:02 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:30:02 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:30:16 backup Keepalived_vrrp[1141]: (VI_1) Master received advert from 172.25.250.101 with higher priority 255, ours 99
Feb 12 05:30:16 backup Keepalived_vrrp[1141]: (VI_1) Entering BACKUP STATE # 此时服务器还是backup状态
Feb 12 05:30:16 backup Keepalived_vrrp[1141]: (VI_1) removing VIPs. # 并移除VIP
Feb 12 05:30:53 backup kernel: perf: interrupt took too long (4036 > 3271), lowering kernel.perf_event_max_sample_rate to 49000
Feb 12 05:36:40 backup systemd[1]: Starting Cleanup of Temporary Directories...
Feb 12 05:36:40 backup systemd[1]: systemd-tmpfiles-clean.service: Succeeded.
Feb 12 05:36:40 backup systemd[1]: Started Cleanup of Temporary Directories.
Feb 12 05:37:59 backup Keepalived_vrrp[1141]: (VI_1) Backup received priority 0 advertisement
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: (VI_1) Receive advertisement timeout # 检查超时,此时因为我们关闭了master的网卡
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: (VI_1) Entering MASTER STATE # 服务器进入master状态进行接管
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: (VI_1) setting VIPs. # 添加VIP
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: (VI_1) Sending/queueing gratuitous ARPs on ens33 for 172.25.250.100
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:00 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:05 backup Keepalived_vrrp[1141]: (VI_1) Sending/queueing gratuitous ARPs on ens33 for 172.25.250.100
Feb 12 05:38:05 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:05 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:05 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:05 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
Feb 12 05:38:05 backup Keepalived_vrrp[1141]: Sending gratuitous ARP on ens33 for 172.25.250.100
LVS+Keepalived实践
采用LVS VS/DR模式+Keepalived
实验拓扑
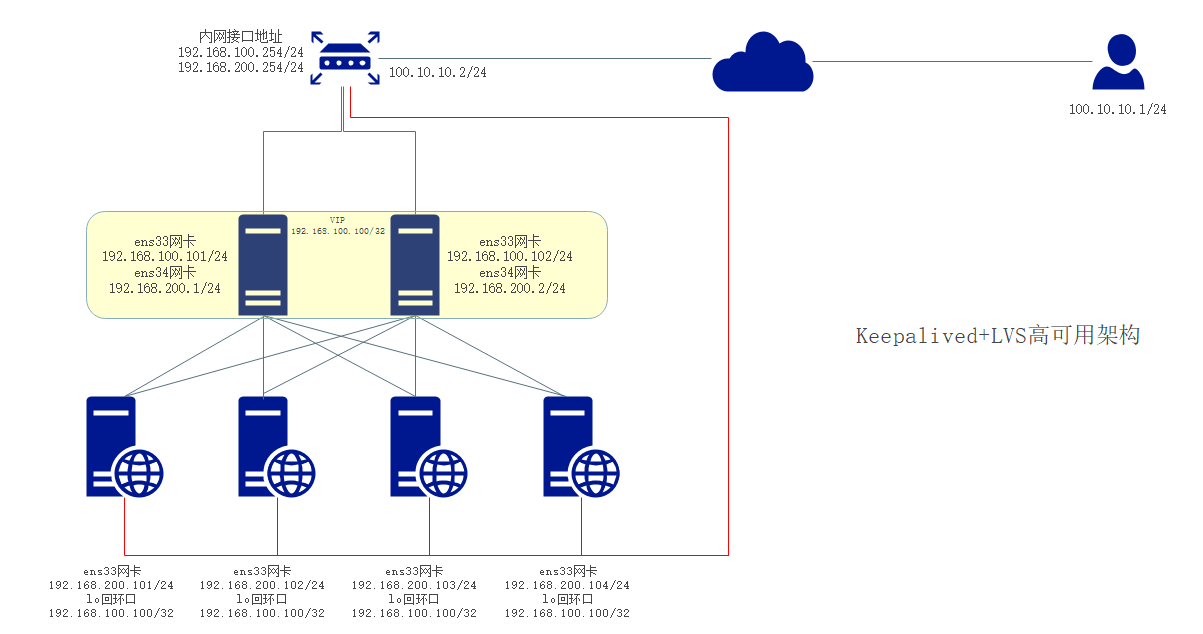
配置环境
四台Web服务器
1
2
3
4
5
6
7
8[root@web01 ~]# vi /etc/sysctl.conf
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.lo.arp_ignore = 1
net.ipv4.conf.all.announce = 2
net.ipv4.conf.lo.announce = 2
[root@web01 ~]# sysctl -p
[root@web01 ~]# ip address add 192.168.100.100/32 dev lo
[root@web01 ~]# ip address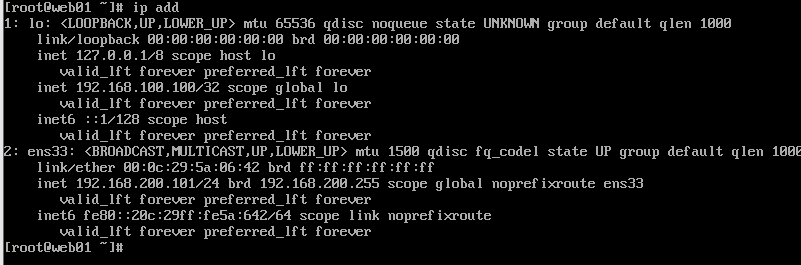
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19[root@web01 ~]# mount /dev/sr0 /mnt/
[root@web01 ~]# tee > /etc/yum.repos.d/a.repo << EOF
[BaseOS]
name = BaseOS
baseurl = file:///mnt/BaseOS
enabled = 1
gpgcheck = 0
[AppStream]
name = AppStream
baseurl = file:///mnt/AppStream
enabled = 1
gpgcheck = 0
EOF
[root@web01 ~]# dnf -y install httpd
[root@web01 ~]# systemctl enable --now httpd
[root@web01 ~]# systemctl disable --now firewalld
[root@web01 ~]# echo "web01" > /var/www/html/index.html
[root@web01 ~]# curl http://localhost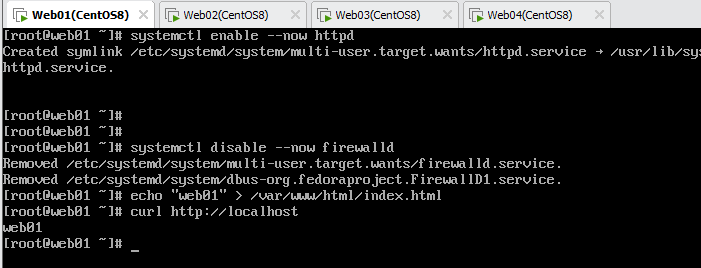
1
2
3
4
5
6
7
8
9
10
11
12
13
14[root@web01 ~]# scp /etc/sysctl.conf 192.168.200.102:/etc/sysctl.conf
[root@web01 ~]# scp /etc/sysctl.conf 192.168.200.103:/etc/sysctl.conf
[root@web01 ~]# scp /etc/sysctl.conf 192.168.200.104:/etc/sysctl.conf
[root@web01 ~]# scp /etc/yum.repos.d/a.repo 192.168.200.102:/etc/yum.repos.d/a.repo
[root@web01 ~]# scp /etc/yum.repos.d/a.repo 192.168.200.103:/etc/yum.repos.d/a.repo
[root@web01 ~]# scp /etc/yum.repos.d/a.repo 192.168.200.104:/etc/yum.repos.d/a.repo
[root@web01 ~]# ssh 192.168.200.102
[root@web02 ~]# sysctl -p
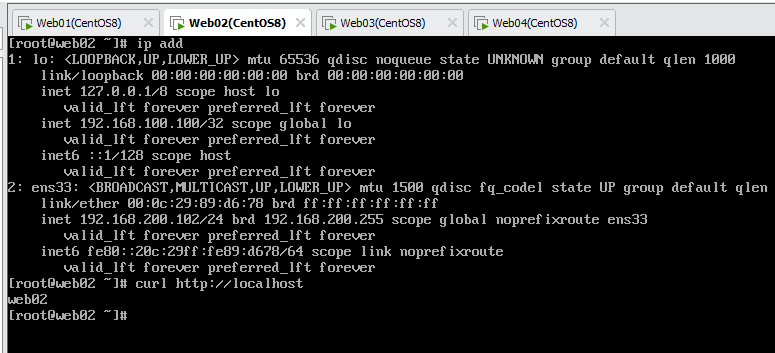
[root@web02 ~]# ip address add 192.168.100.100/32 dev lo
[root@web02 ~]# mount /dev/sr0 /mnt
[root@web02 ~]# dnf -y install httpd
[root@web02 ~]# systemctl enable --now httpd
[root@web02 ~]# systemctl disable --now firewalld
[root@web02 ~]# curl http://localhost
1
2
3
4
5
6
7
8
9[root@web02 ~]# ssh 192.168.200.103
[root@web03 ~]# sysctl -p
[root@web03 ~]# ip address add 192.168.100.100/32 dev lo
[root@web03 ~]# mount /dev/sr0 /mnt/
[root@web03 ~]# dnf -y install httpd
[root@web03 ~]# systemctl enable --now httpd
[root@web03 ~]# systemctl disable --now firewalld
[root@web03 ~]# echo "web03" > /var/www/html/index.html
[root@web03 ~]# curl http://localhost
1
2
3
4
5
6
7
8
9[root@web03 ~]# ssh 192.168.200.104
[root@web04 ~]# mount /dev/sr0 /mnt
[root@web04 ~]# sysctl -p
[root@web04 ~]# ip add add 192.168.100.100/32 dev lo
[root@web04 ~]# dnf -y install httpd
[root@web04 ~]# systemctl enable --now httpd
[root@web04 ~]# systemctl disable --now firewalld
[root@web04 ~]# echo "web04" > /var/www/html/index.html
[root@web04 ~]# curl http://localhost
配置Keepalived(Master)+LVS
IP配置略
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50[root@master ~]# scp 192.168.200.101:/etc/yum.repos.d/a.repo /etc/yum.repos.d/a.repo
[root@master ~]# mount /dev/sr0 /mnt
[root@master ~]# systemctl disable --now firewalld
[root@master ~]# echo "1" > /proc/sys/net/ipv4/ip_forward
[root@master ~]# dnf -y install keepalived
[root@master ~]# dnf -y install vim
[root@master ~]# cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak
[root@master ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id master
}
vrrp_instance VI_1 {
state MASTER
interface ens33
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.100.100
}
}
virtual_server 192.168.100.100 80 {
delay_loop 6
lb_algo rr
lb_kind DR
persistence_timeout 50
real_server 192.168.200.101 80 {
weight 1
}
real_server 192.168.200.102 80 {
weight 1
}
real_server 192.168.200.103 80 {
weight 1
}
real_server 192.168.200.104 80 {
weight 1
}
}
[root@master ~]# systemctl enable --now keepalived配置Keepalived(Backup)+LVS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48[root@backup ~]# mount /dev/sr0 /mnt/
[root@backup ~]# scp 192.168.100.101:/etc/yum.repos.d/a.repo /etc/yum.repos.d/a.repo
[root@backup ~]# systemctl disable --now firewalld
[root@backup ~]# echo "1" > /proc/sys/net/ipv4/ip_forward
[root@backup ~]# dnf -y install vim keepalived
[root@backup ~]# scp 192.168.100.101:/etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf
[root@backup ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id backup
}
vrrp_instance VI_1 {
state BACKUP
interface ens33
virtual_router_id 51
priority 99
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.100.100
}
}
virtual_server 192.168.100.100 80 {
delay_loop 6
lb_algo rr
lb_kind DR
persistence_timeout 50
real_server 192.168.200.101 80 {
weight 1
}
real_server 192.168.200.102 80 {
weight 1
}
real_server 192.168.200.103 80 {
weight 1
}
real_server 192.168.200.104 80 {
weight 1
}
}
[root@backup ~]# systemctl enable --now keepalived配置网关及Nat
- 配置网卡
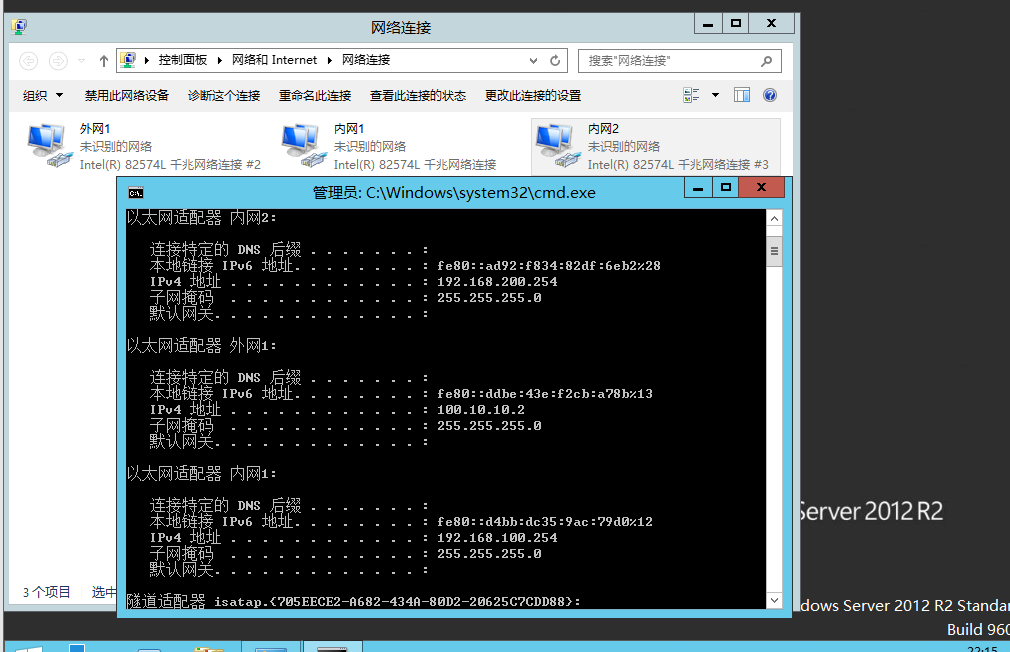
安装服务
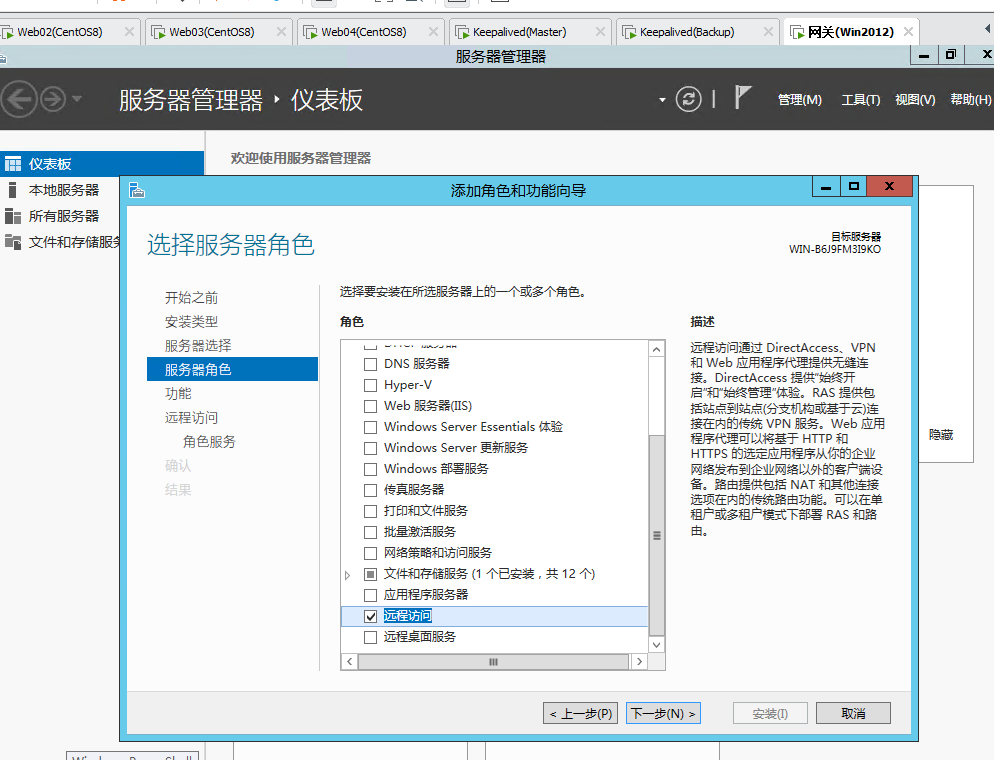
选择路由然后一下步直至安装完毕
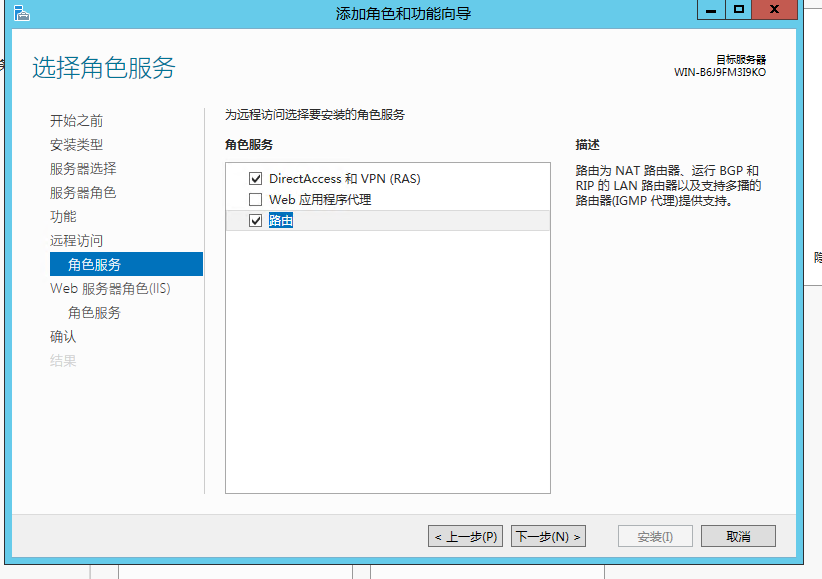
安装好之后配置NAT
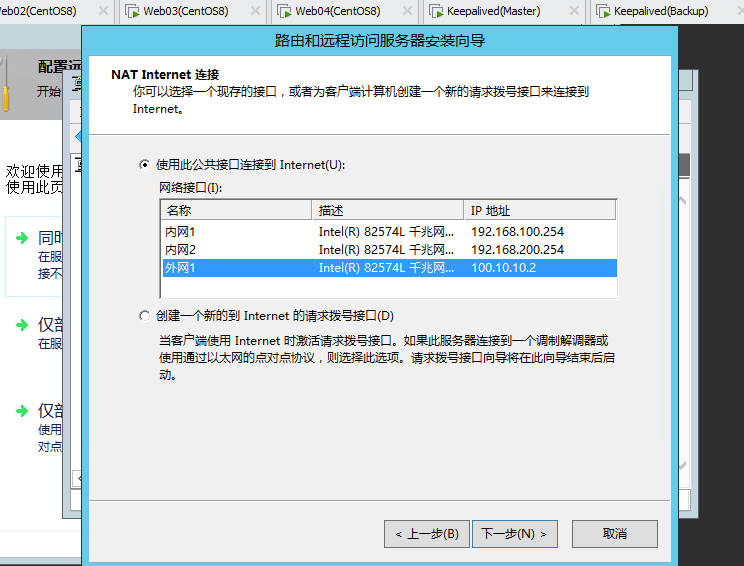
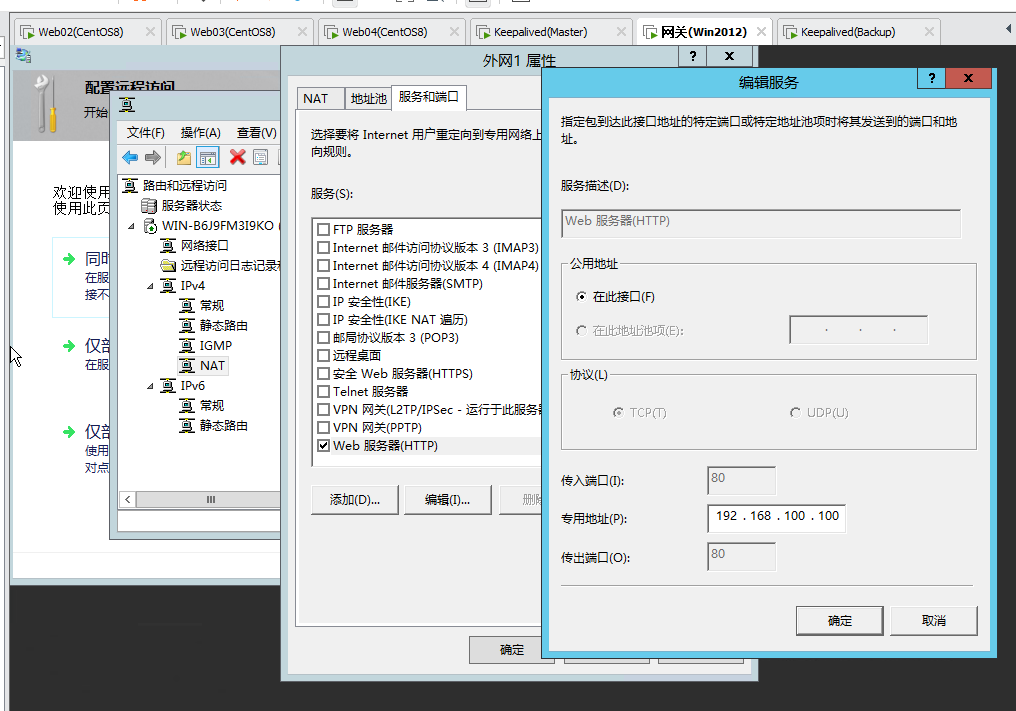
测试
IP地址随意,不一定按照拓扑图上来
我这测试的情况是一台主机发送请求后一直对应后端的Web02服务器,更换IP后后端Web才变
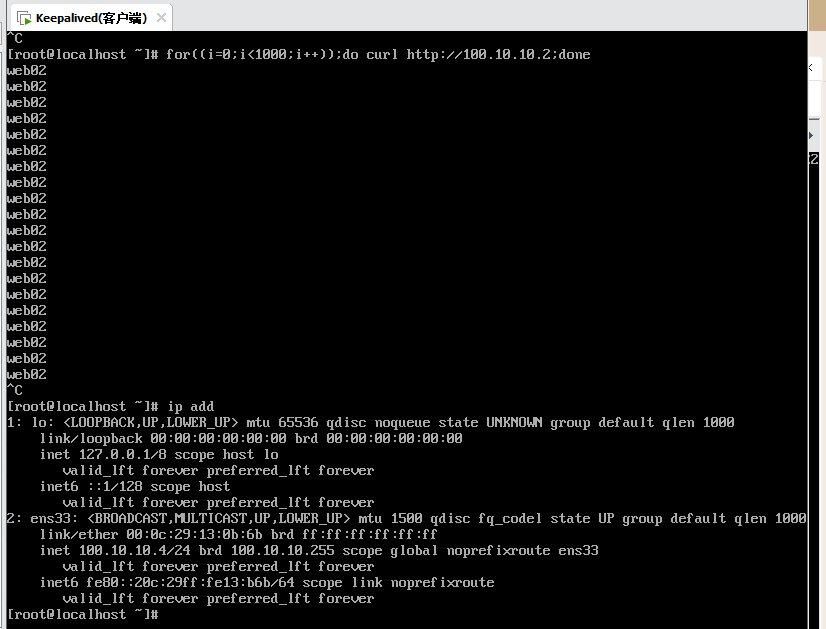
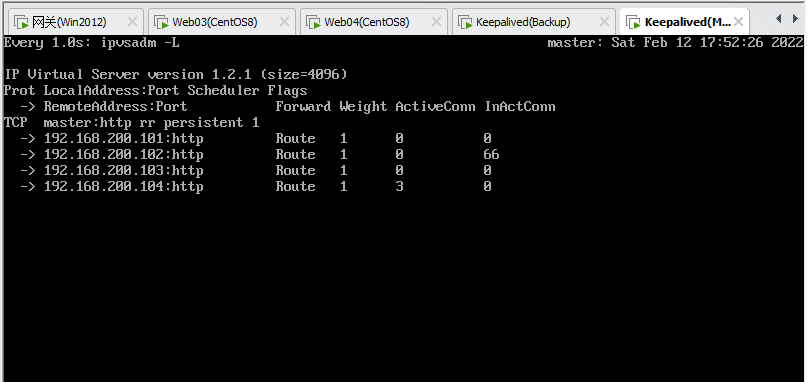
断开Master网卡
1
[root@master ~]# nmcli connection down ens33
再次访问(结果正常,实现了LVS的高可用)
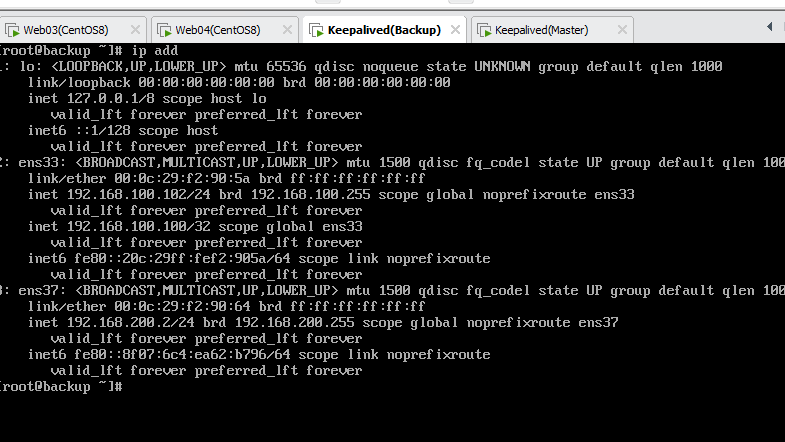
- Backup正常接管VIP
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 尤妤!





